Home / journal
Success Story
Enhancement and Improvement AWS Landing Zone
Executive Summary
The Bank accelerated its digital transformation by adopting a secure, scalable and manageable cloud infrastructure through the implementation of AWS Landing Zone. This strategic initiative lays the foundation for modern banking services, operational agility and regulatory compliance in the cloud. The Bank currently has an AWS Landing Zone, the Bank has 7 accounts, but all accounts have not been assigned to their respective OUs.Customer Challange
To support security in today's digital era, the availability of services is very important, be it a Data Centre, Server devices or other supporting services, so that customers feel comfortable and happy using these services. As the Bank transitioned to a cloud-first model, it faced some key challenges that had to be overcome to ensure a secure, compliant and effective AWS Landing Zone implementation. These challenges were both technical and organisational, reflecting the complexity of modern banking operations in a regulated environment.Solution
PT. Mastersystem Infotama Tbk as Amazon AWS Partner, provides improvements to the existing AWS Landing Zone with AWS Best Practices standard. Which is where the Landing Zone becomes feasible in terms of compliance and governance from the Bank. The following Account Structure improved from Mastersystem from the previous hierarchy at the same level for all AWS accounts: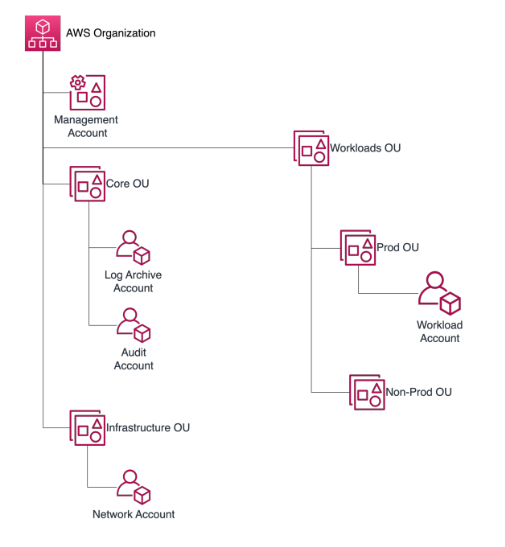
AWS Landing Zone which was previously created manually, Mastersystem made improvements to the AWS Landing Zone using the AWS Control Tower Service with the following High Level Diagram:
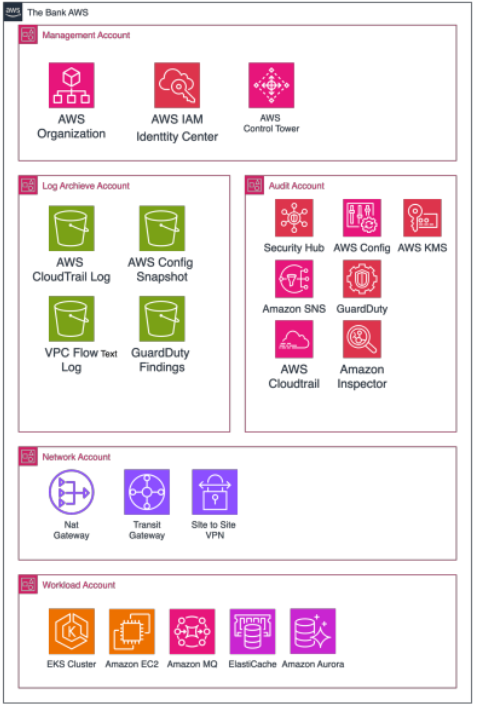
As part of the governance enhancement, AWS Control Tower is activated in the Management Account to upgrade from the previous AWS Landing Zone setup. This enables automated, scalable governance for a multi-account environment. Within the AWS Organization, Service Control Policies (SCPs) are enabled to enforce account-level restrictions and align with the Bank’s security and compliance standards. IAM Identity Center is used to centrally manage user access with Single Sign-On (SSO) and Role-Based Access Control (RBAC), and Multi-Factor Authentication (MFA) is enforced across all users. In the Audit Account, key AWS security services such as AWS Security Hub, Amazon GuardDuty, AWS CloudTrail, and Amazon Inspector are activated to provide centralized threat detection and auditing. The Log Archive Account is set up as the central logging repository using Amazon S3, collecting logs from all accounts in the organization for auditing and compliance. The Network Account continues to host shared networking services, including NAT Gateway, Transit Gateway, and Site-to-Site VPN, which are shared with workload accounts. This structure ensures centralized, secure, and efficient cloud management using AWS Organizations.
Benefit and Result
From the enhancement and improvement of AWS Landing Zone by AWS Control Tower, The Bank has met the standardization of compliance and governance based on AWS Best Practices. The Bank was able to save up to 80% time for OU and AWS Account creation, SCP setup, Logging, IAM Automation & integration as well as in AWS Services validation & testing.Newsletter - Stay tune and get the latest update
Far far away, behind the word mountainsCopyright ©2024 All rights reserved | PT Mastersystem Infotama
